Reading this recent Wall Street Journal article about Apple’s push to drive adoption of their Vision Pro “spatial computers” in the enterprise got me thinking: Can VR headsets really make the leap from a cool gadget to a serious business tool? The potential is exciting—imagine the possibilities for collaboration and training. But then my security-focused brain kicked in. How do we manage the risks that come with introducing these powerful devices into the workplace?
I think we’ve all experienced that blurring of the lines between our personal and work lives, especially when it comes to our devices. Finding ways to protect our data while still leveraging the potential productivity boost from devices like the Apple Vision Pro is a challenge we all face as network security practitioners.
How Netskope secures the Apple Vision Pro
Intrigued by the possibilities (and let’s be honest, who here isn’t intrigued by shiny new tech?), I got my hands on the Vision Pro and set to work to see if I could get real work done on it securely. Let’s explore two scenarios where the Netskope Client can be leveraged on the Apple Vision Pro:
Scenario 1: Safe browsing
Imagine an employee receives a link in a Microsoft Teams message. It appears legitimate, but unknowingly, the link might conceal malware. With the Netskope Client installed on the Vision Pro, clicking the link triggers a redirection to an isolated browser environment. The employee can browse the content with the assurance that any potential threats will be contained.

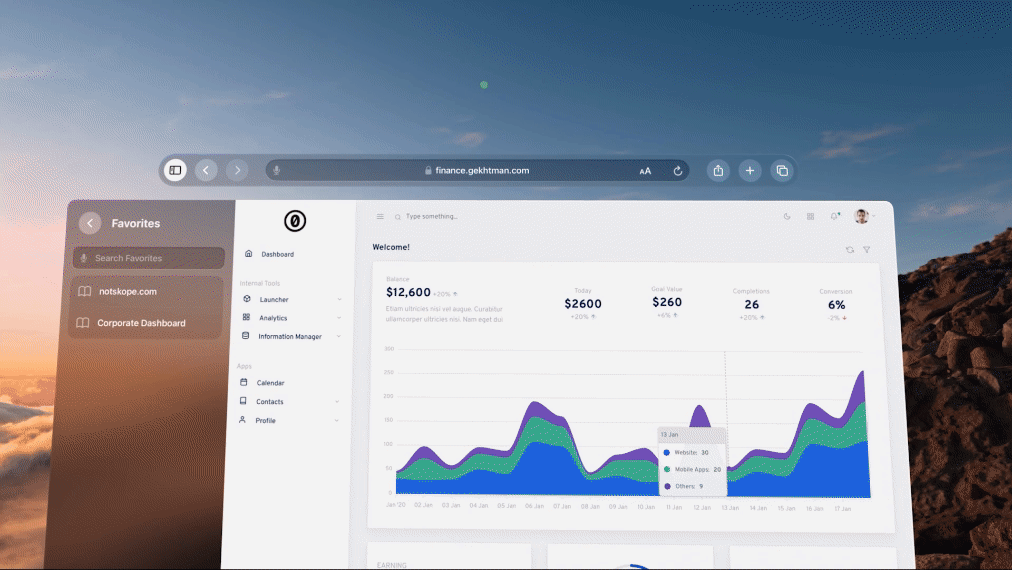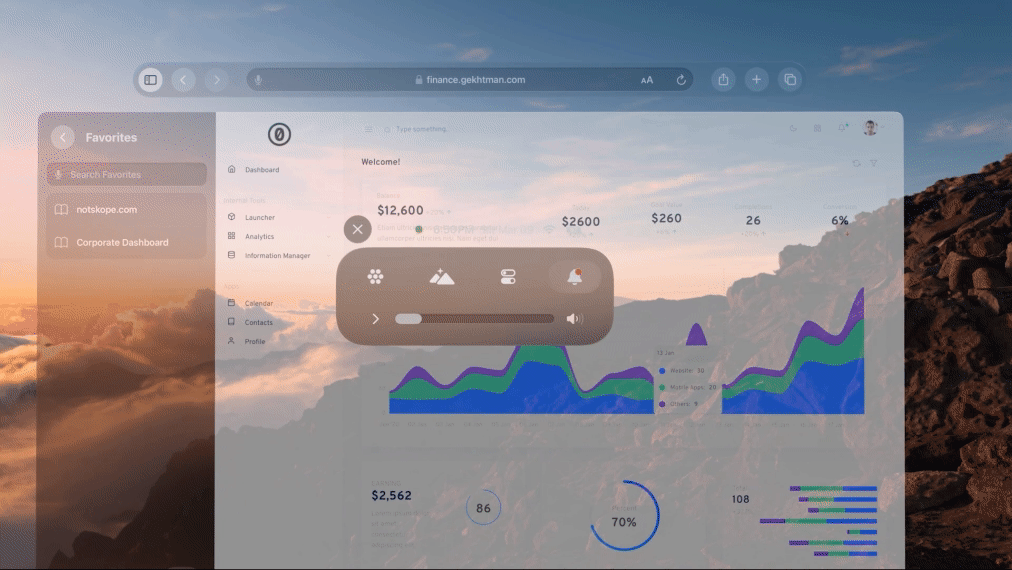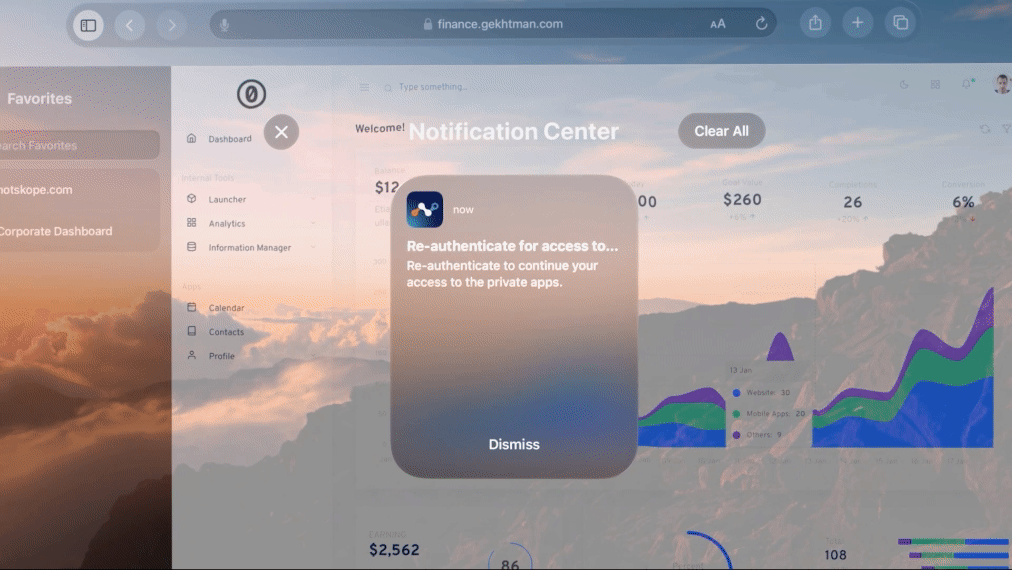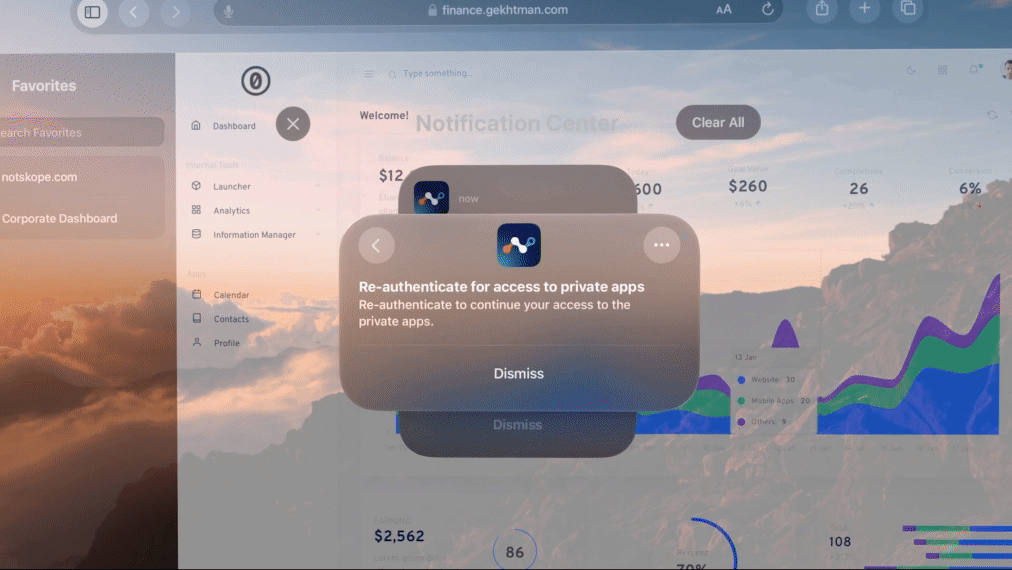
Scenario 2: Secure Access to Private Apps
An employee needs access to an internal application, such as a revenue reporting tool, from their headset. The Netskope Client installed on the Apple Vision Pro allows for zero trust-based access to the company resource and enforces continuous trust verification. Periodically, the employee must re-authenticate, ensuring that the human trying to access the application is always an authorized user.
If I’ve piqued your interest, check out the full demo video here.
Why this matters
Modern data protection perimeters are constantly expanding with the introduction of new technologies and any device capable of accessing corporate tools increases your attack surface. This makes a zero trust architecture essential for mitigating common risk vectors, like these:
- Threat prevention: A single malware infection or successful phishing attack on a single device can compromise your entire network. Attackers need only one entry point to gain a foothold in your systems to move laterally and steal sensitive data.
- Data loss: From accidental/intentional oversharing, misuse of personal accounts, to malicious intent (e.g., disgruntled employees), data leaks can happen in countless ways with potentially devastating impact.
- Compliance: Regulations demand robust device security. Failure to comply risks hefty fines and irreversible reputational damage.
At Netskope, we believe that users, devices, and data deserve enterprise-grade protection wherever they go. The Netskope One platform makes this possible. Our patented Zero Trust Engine, Intelligent SSE, and the NewEdge network empower network security teams to defend their businesses and protect their data.
Experience Netskope: Register for our Tech Day Workshop at the RSA Conference
We understand the challenges of securing personal devices in the workplace. That’s why we invite you to register for our Tech Day Workshop at the RSA Conference, where we’ll dive deep into emerging technologies like the Apple Vision Pro, GenAI, and more.
Bonus: Visit us at Booth #1035, Moscone Center, at the RSA Conference to learn how to implement a zero trust architecture with the Netskope One Platform.




 Back
Back 





















 Read the blog
Read the blog